Projects
Page
This website page is dedicated to the various projects i have completed, below are descriptions and links to my projects that students and anyone intrested may view.
Mobile Forensics Research Paper
Digital forensics and its presence within criminal cases has become more apparent with the rise of globalisation and the reduction in cost of technology. This has empowered individuals to access services and tools that enhance their work, daily lives and communication. Simultaneously, this places technology in the hands of criminals, thus requiring a form of device analysis in most criminal cases. Due to the software support the android operating system exhibits, individuals can freely create applications that collect a great deal of data or actively avoid collection. To the consumer, this is a blessing and a curse with the rise of privacy concerns and the constant need for better software and features. In regards to forensics, this creates a nightmare for data acquisition during cases with strict triage guidelines; as the overlapping of data creates more entries that must be organised into artefacts and non-artefacts. There is also a concern for a lack of artefacts that inhibit device attribution such as apps similar to signal, secure folder and telegram. This constant evolving software and hardware landscape requires a need for continuous improvement in forensic tools and techniques. The purpose of this report is to depict the process of artefact acquisition using various tools and methods. Access the document using this link.
AWS Network Design and implementation
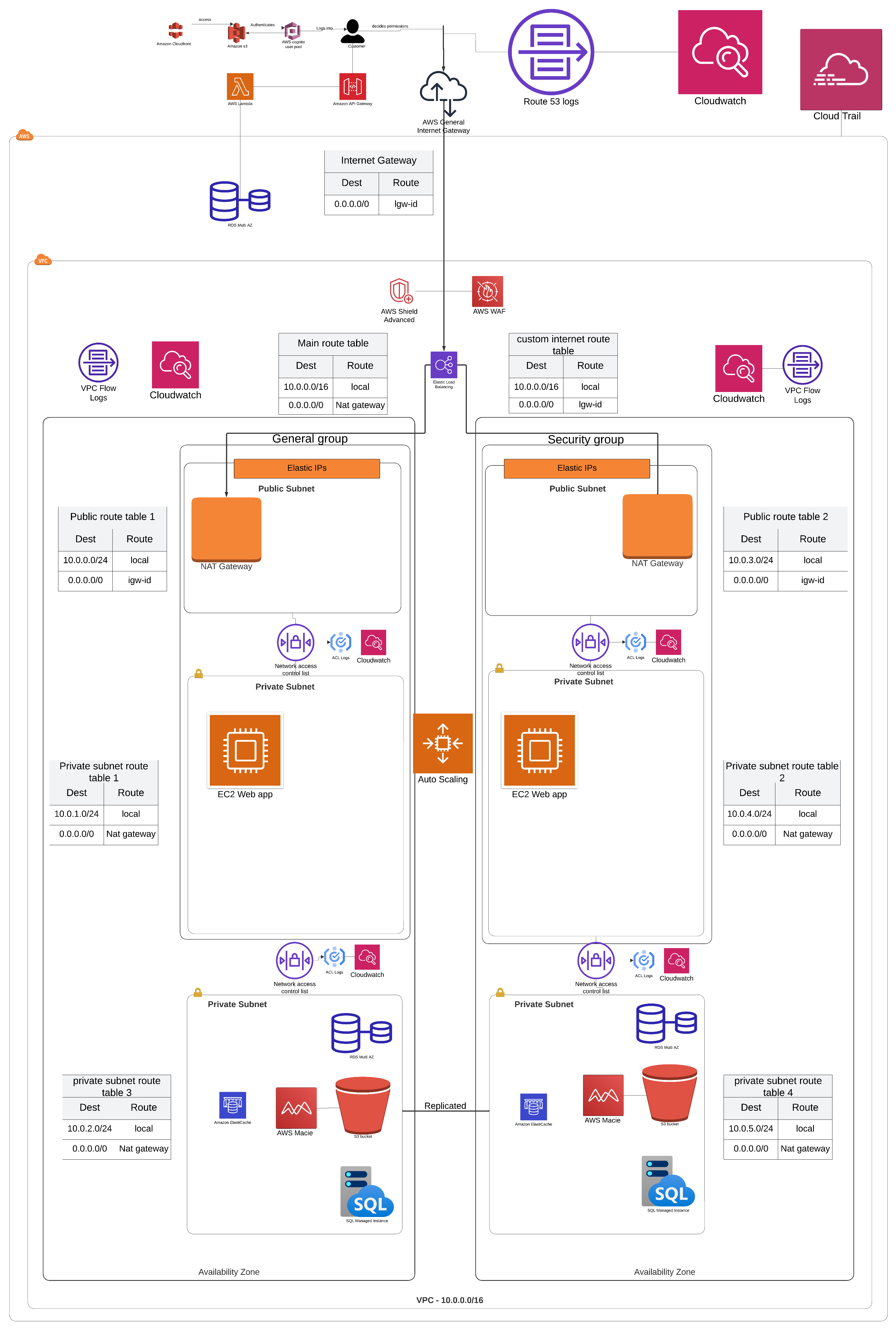
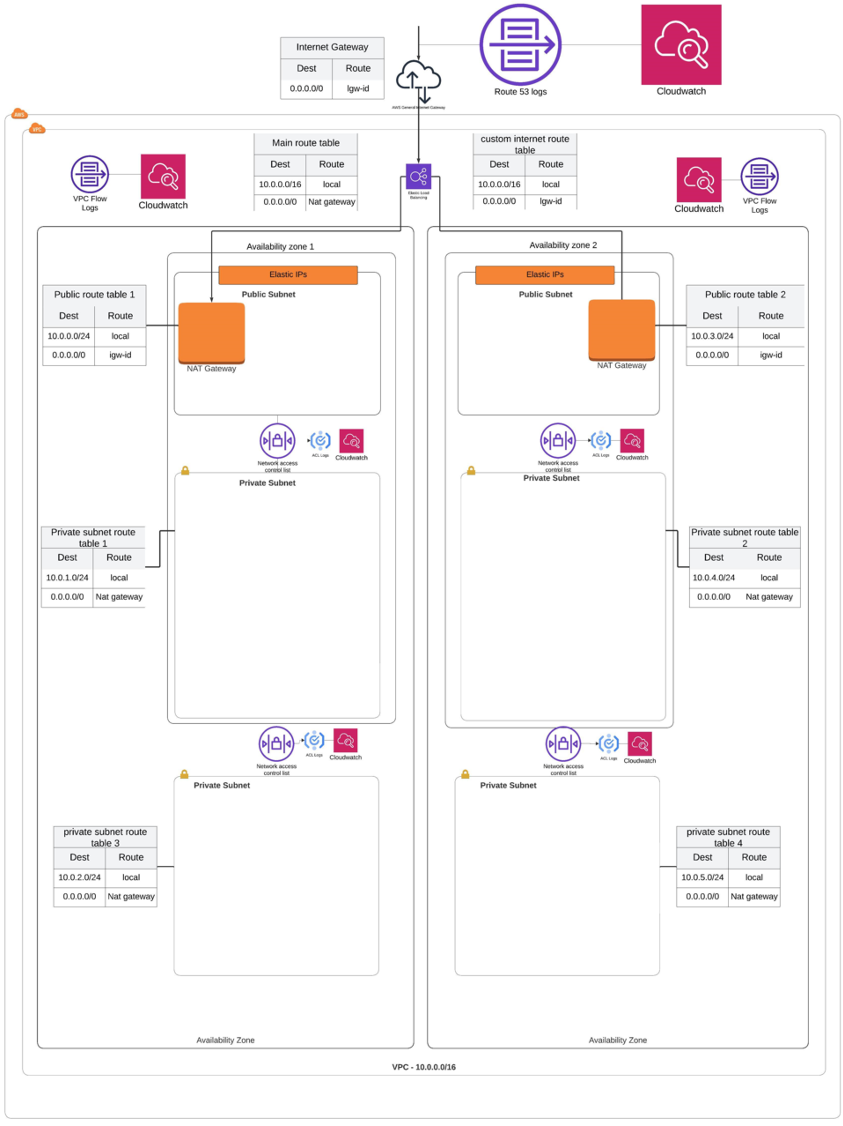
Designed and implemented a secure network using AWS cloud solution. The design focuses on a high availability and secure network for a financial web application. The design was then built and tested using a sandbox environment.
It is important to recognise the trend in organisations migrating their networking architecture to the cloud through various service providers such as google cloud and Amazon web services. As cloud services become more available, cost-effective and a more convenient option for business; there will be a gradual increase in threats and concerns relating to cloud migration from on premises storage. An Introductory report has been written that includes why businesses migrate to the cloud and the possible security, legal and operational implications the process has on businesses. This report which can be found here outlines the technical and organisational consequences of the cloud; as well as the roles and responsibilities parties must fulfill for a successful migration.
A breif breakdown and rational of the network strucutre is outlined below. Instructions on how to implement each part of the network are included as well in this document.
Spam filter
An AI spam filter was developed and tested using various machine learning algorithms to detect and filter spam and phishing emails.
The purpose of this project is to develop modern and relevant defences against common phishing/spam email attacks. According to modern risk assessment tools and approaches, employees are statistically the most at risk with one of the largest financial and operational impacts from a cyber attack. 91% of all cyber attacks begin with a phishing email to an unexpected victim, depicting its scalability and mass application. Due to employees’ general high level clearance and access to sensitive information, phishing/email attacks have historically been the most successful throughout all levels of management as a result of its simplicity. Therefore it is imperative to provide a potential automated solution as organisations increase workforce.
Attacking an AI
I conducted an Adversarial attack on a deep learning neural network.
Due to the wider adoption of AI, it is important to understand how these LLM process information to achieve a desired output. Therefore, AI can be designed in such as way to prevent various attacks on the nueral network; this is especially important as the algorithm may provide core features that enable a product or provide it with a competitive edge. With the implementation of algorthms such as ChatGTP, Gemini and co-pilot; it risks innaccurate/useless outputs that may harm business image or consumers by bad actors attacking the algorithm through an adversarial attack explored within this project summary.